HTTP Strict Transport Security (HSTS)
Enroll to start learning
You’ve not yet enrolled in this course. Please enroll for free to listen to audio lessons, classroom podcasts and take practice test.
Interactive Audio Lesson
Listen to a student-teacher conversation explaining the topic in a relatable way.
Introduction to HSTS
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Today, we're going to talk about HTTP Strict Transport Security, or HSTS for short. Can anyone tell me why HTTPS is important?

It encrypts the data between the browser and the server, right?

Exactly! HSTS takes it a step further by enforcing that all communications must be secure. It prevents scenarios where an attacker could force a connection to fall back to HTTP. What do you think would happen if such an attack were successful?

Sensitive data could be intercepted!

That's correct! This is why HSTS is essential. Remember the acronym HSTS—H for enforce HTTPS, T for transport security, S for strict. Can someone explain what HSTS necessitates for web developers?

They must configure their web server to include the HSTS header in the responses.

Great! And what does the header look like?

It includes directives like max-age!

Exactly right! HSTS is easy to implement but has significant implications for security.
Implementing HSTS
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Now that we understand what HSTS is, let's discuss how to implement it effectively. Can anyone recall the directive that specifies how long browsers should remember to enforce HSTS?

It's max-age!

Correct! The max-age directive is crucial. How might a developer use it in practice?

They might set it to a long duration, like one year, to ensure the policy sticks!

Excellent point! Remember, it's best practice to include `includeSubDomains` when setting HSTS. Why do you think that is?

To protect subdomains, too!

Absolutely! By ensuring all subdomains are included, we protect the entire domain. What about the importance of enabling HSTS preloading?

It helps browsers know to use HTTPS before even making the request?

Precisely! Enabling preloading can greatly improve security for new users.
Benefits of HSTS
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Moving on, let’s talk about the benefits of HSTS. How does enabling HSTS impact the security of an application?

It ensures that data is always encrypted during transmission!

Exactly! It also reduces the risk of man-in-the-middle attacks and ensures user trust. Can anyone think of potential challenges when using HSTS?

If a developer misconfigures it, users may be locked out if they try to access the site via HTTP.

That's a critical point! Misconfiguration can lead to user experience issues. It’s important to thoroughly test HSTS settings before going live.

And also, developers should be aware that once HSTS is enabled, it can be hard to reverse.

Correct! That’s why HSTS should be carefully planned and implemented.
Introduction & Overview
Read summaries of the section's main ideas at different levels of detail.
Quick Overview
Standard
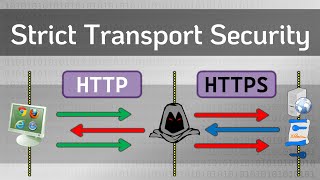
HTTP Strict Transport Security (HSTS) is a crucial security header that instructs browsers to only connect to a site using HTTPS. This prevents man-in-the-middle attacks and increases the overall security posture of web applications by ensuring that sensitive data is always transmitted securely.
Detailed
HTTP Strict Transport Security (HSTS)
HSTS (HTTP Strict Transport Security) is a web security policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. By enabling HSTS on a domain, web developers can ensure that browsers only interact with the server over HTTPS, thus encrypting all data transmitted between the browser and the server.
Key Features of HSTS
- Mandatory HTTPS: HSTS forces web browsers to only establish secure HTTPS connections to the server, preventing attackers from intercepting sensitive information.
- Implementation: This is achieved by adding the
Strict-Transport-Securityheader to the response from the server. This header can include directives likemax-age, which specifies the time in seconds for which the browser should remember to enforce the policy. - Security Benefits: By strictly enforcing HTTPS, HSTS greatly enhances the security of web applications, mitigating potential vulnerabilities that arise when using plain HTTP.
Importance in Web Security
As full stack web developers, implementing HSTS is part of a broader strategy to enhance application security, safeguarding user data and building trust. HSTS is particularly important for applications that handle sensitive information, ensuring that data integrity and confidentiality are maintained.
Youtube Videos

Audio Book
Dive deep into the subject with an immersive audiobook experience.
Introduction to HSTS
Chapter 1 of 2
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
HSTS forces browsers to only communicate with your site over HTTPS. It’s a simple but crucial header to include:
Detailed Explanation
HTTP Strict Transport Security (HSTS) is a security feature that directs web browsers to only connect to a server using HTTPS, rather than HTTP. This helps to protect users by preventing man-in-the-middle attacks, which can occur when an attacker tries to intercept the communication between the user and the server. By enforcing HTTPS, HSTS ensures that all data exchanged is encrypted, providing a secure connection.
Examples & Analogies
Think of HSTS as a security guard at the entrance of a secured building. Just like the guard would only allow entry through a secure door (HTTPS), HSTS ensures that data can't be transmitted through a potentially unsafe channel (HTTP). This protects everything that happens inside the building (user data) from prying eyes.
Implementing HSTS
Chapter 2 of 2
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
Strict-Transport-Security: max-age=31536000; includeSubDomains;
Detailed Explanation
The implementation of HSTS involves sending a specific HTTP header from your server to the browser. The header example given is 'Strict-Transport-Security: max-age=31536000; includeSubDomains;'. The 'max-age=31536000' means that the browser should remember this preference for one year (31,536,000 seconds). The 'includeSubDomains' directive indicates that this policy applies not just to the main domain, but also to any subdomains. By implementing this header, you instruct browsers to always use HTTPS for your site, enhancing security.
Examples & Analogies
Imagine you have a parking permit that allows you to park your car in any parking lot owned by a specific company for a full year. Similarly, the HSTS max-age directive signals to the browser that it should always use the secure parking lot (HTTPS) for a whole year. The 'includeSubDomains' part ensures that even if you visit a different branch of the same parking company (subdomain), you’re still parked securely.
Key Concepts
-
HSTS: Enforces mandatory HTTPS for secure communications.
-
max-age: Specifies duration for which HSTS is enforced.
-
includeSubDomains: Directive to include all subdomains under HSTS.
Examples & Applications
A website that implements HSTS will only connect clients using HTTPS, preventing attackers from downgrading connections.
By leveraging HSTS properly, a developer can ensure that a user’s confidential information is not exposed during network transmission.
Memory Aids
Interactive tools to help you remember key concepts
Rhymes
HSTS, here to save the day, prevents the downgrade, come what may!
Stories
Imagine if every time you enter a secure building, the door could be unlocked by someone outside. HSTS locks that door and only lets trusted keys in!
Memory Tools
Remember HSTS: H - Only use HTTPS, S - Strictly enforced, T - Transport security.
Acronyms
HSTS
- Secure Hypertext
- Strict
- Transport
- Security.
Flash Cards
Glossary
- HSTS
HTTP Strict Transport Security, a security feature enforcing secure HTTPS connections.
- maxage
A directive indicating how long browsers should remember to enforce HTTPS connections.
- includeSubDomains
A directive that extends HSTS to all subdomains of the specified domain.
Reference links
Supplementary resources to enhance your learning experience.
