Challenges and Design Considerations
Interactive Audio Lesson
Listen to a student-teacher conversation explaining the topic in a relatable way.
Understanding Latency Challenges
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Today, let's talk about latency. What do you think happens if our system takes too long to respond to an input signal?

It might make the system feel slow or unresponsive!

And in real-time applications, it could lead to serious issues, right?

Exactly! We need to ensure low latency through strategies like using low-latency Interrupt Service Routines or DMA. Can anyone tell me how DMA works?

Isn't it where peripherals transfer data directly to memory, bypassing the CPU?

Great job! This reduces the CPU's workload and minimizes latency. Remember the acronym 'IDLE' for Interrupts and DMA for Low-latency Efficiency. Let's summarize: managing latency is crucial because delays can affect system functionality.
Priority Inversion Impact
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Now, let's explore priority inversion. Who can explain what it is?

It’s when a higher-priority task waits for a lower-priority task to finish, right?

Spot on! This can lead to missed deadlines. Can anyone suggest how we might alleviate this issue?

I think implementing priority inheritance could help!

Correct! By temporarily raising the lower-priority task’s priority, we can help it finish sooner. As a mnemonic, think 'Keep Priority High' to remember this strategy. To wrap up, managing priorities is vital to ensure deadlines are met.
Buffer Management Techniques
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Let's move on to buffer overflows. What happens if a buffer gets too full?

It can cause the system to crash or lose data!

How do we prevent that from happening?

Excellent question! We need to properly size our buffers and use flow control mechanisms. What's a good way to remember this?

How about 'Size Matters'?

Perfect! Summary: Avoiding buffer overflows requires careful sizing and control to effectively manage data flow.
Dealing with Noise and Errors
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Finally, let’s discuss noise and error handling. What is the impact of noise in data transmission?

It can corrupt the data being sent, which could lead to mistakes in operations.

Exactly! How might we handle this?

Using checksums or CRC to validate data, right?

Absolutely! CRC is a great way to detect errors. And for a memory aid, think 'Correct Receivers Check' when using CRC. To summarize: robust error handling is crucial for reliable data communication.
Introduction & Overview
Read summaries of the section's main ideas at different levels of detail.
Quick Overview
Standard
In embedded systems, designers face various challenges related to I/O operations such as latency, priority inversion, buffer overflows, and noise/error handling. This section outlines effective strategies to manage these challenges, including low-latency ISRs, priority inheritance, and robust protocols.
Detailed
Challenges and Design Considerations
In real-time and embedded systems, managing Input/Output (I/O) operations presents several challenges that need careful consideration to ensure the system operates effectively and efficiently. This section elaborates on key challenges and associated strategies, providing insights into optimum design considerations for I/O management.
Key Challenges in I/O Management
- Latency: Low latency is essential for real-time performance. Delays in processing input or output can lead to unacceptable system performance, impacting functionality.
- Priority Inversion: It occurs when a higher-priority task is waiting for a lower-priority task to release a resource, leading to potential deadlocks or delayed responsiveness.
- Buffer Overflows: If the data being received exceeds the allocated buffer size, it can cause system crashes or data corruption.
- Noise/Error Handling: External noise can corrupt data, necessitating robust error detection and correction mechanisms.
Strategies to Manage Challenges
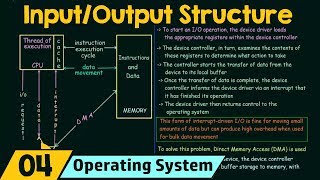
- Low Latency ISRs and DMA: Using low-latency Interrupt Service Routines (ISRs) and Direct Memory Access (DMA) reduces latency by allowing faster data handling directly between peripherals and memory without CPU intervention.
- Priority Inheritance: Implementing priority inheritance can help mitigate priority inversion by temporarily raising the priority of a task holding a resource required by a higher-priority task.
- Buffer Management: Proper buffer sizing is crucial, along with flow control mechanisms to prevent data loss and ensure that the system can handle bursts of data without overflow.
- Noise/Error Control: Employing techniques like Cyclic Redundancy Check (CRC), retries, and robust communication protocols can reduce the impact of noise in data transmission.
These strategies are fundamental in designing reliable, efficient embedded systems capable of handling the rigorous demands of I/O operations.
Youtube Videos



Audio Book
Dive deep into the subject with an immersive audiobook experience.
Latency Challenges
Chapter 1 of 4
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
Latency: Use low-latency ISRs and DMA
Detailed Explanation
Latency refers to the delay between a request for action (like pressing a button) and the system's response. In embedded systems, this can be critical. To manage latency effectively, developers use low-latency Interrupt Service Routines (ISRs), which are quick responses to interrupts from hardware. Additionally, Direct Memory Access (DMA) allows peripherals to communicate with memory without involving the CPU, which speeds up data transfer and reduces the time the system takes to respond.
Examples & Analogies
Consider a traffic light system. If the light takes too long to change after a pedestrian presses the button, it creates frustration. Low-latency ISRs are like having a traffic manager who immediately responds to the button press, while DMA is akin to a direct communication line that allows information about traffic flow to be transferred quickly without unnecessary delays.
Priority Inversion Challenges
Chapter 2 of 4
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
Priority Inversion: Use priority inheritance
Detailed Explanation
Priority inversion occurs when a lower-priority task holds a resource needed by a higher-priority task, preventing it from executing. To mitigate this, the priority inheritance mechanism is employed, temporarily raising the priority of the lower-priority task to that of the higher one when it holds the shared resource. This helps ensure that critical tasks can proceed without undue delay.
Examples & Analogies
Imagine a situation where a fire truck (high-priority) is stuck behind a slow delivery truck (low-priority) because the road is blocked. If we can temporarily allow the delivery truck to move faster when it's blocking the fire truck, the emergency response can happen more swiftly. This is what priority inheritance does in a system.
Buffer Overflow Challenges
Chapter 3 of 4
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
Buffer Overflows: Use proper buffer sizing and flow control
Detailed Explanation
Buffer overflows occur when data exceeds the allocated buffer size in memory, which can corrupt data or crash the system. To prevent this, proper buffer sizing is crucial to ensure that buffers can handle maximum anticipated data sizes. Additionally, implementing flow control mechanisms, like acknowledgments from the receiving end before transmitting more data, can help manage the smooth flow of information.
Examples & Analogies
Think of a sink (the buffer) that can only hold a certain volume of water. If you keep pouring water without stopping, it will overflow. By ensuring that you only pour a specific amount of water at a time (flow control) and using a bigger sink if necessary (proper sizing), we can prevent overflowing and maintain order.
Noise and Error Handling Challenges
Chapter 4 of 4
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
Noise/Error Handling: Use CRC, retries, and robust protocols
Detailed Explanation
Noise and interference can corrupt data during transmission in embedded systems. To handle such situations, cyclic redundancy check (CRC) codes are often employed to detect any corruption. If errors are detected, data can be retransmitted (retry mechanism), and developing robust transmission protocols can help ensure that communication remains reliable under adverse conditions.
Examples & Analogies
Imagine sending a letter (data) through a postal system prone to misdelivery (noise). To ensure the letter reaches the right person without errors, you’d include a return receipt to confirm it was delivered (CRC) and have a policy to resend it if it never arrived (retry). Robust protocols act like clear postal rules, ensuring that your mail gets where it needs to go correctly.
Key Concepts
-
Low Latency: Strategies to minimize delays in embedded systems are essential for timely input/output processing.
-
Priority Inversion: A critical issue affecting system responsiveness that can be managed through priority inheritance techniques.
-
Buffer Management: Essential for preventing data loss due to overflow; requires proper sizing and control.
-
Error Handling: Robust protocols are necessary to deal with noise and data corruption in communication.
Examples & Applications
Using DMA to transfer data from a sensor to memory without CPU intervention, improving response time.
Implementing priority inheritance in an RTOS to manage tasks efficiently and avoid priority inversion.
Memory Aids
Interactive tools to help you remember key concepts
Rhymes
Latency's no friend, it delays our speed, make ISRs fast to succeed!
Stories
Imagine a traffic jam where higher cars are stuck behind lower ones—this is priority inversion and it needs to be resolved for smooth traffic flow!
Memory Tools
Remember 'SIZE' for buffer management: Sizing, Inflow control, Zero overflows, Efficiency.
Acronyms
N.E.E.D. for Noise Error Efficiency Design
Noise check
Error correction
Efficient communication
Design integrity.
Flash Cards
Glossary
- Latency
The delay between input and output processing that affects the system's responsiveness.
- Priority Inversion
A scenario where a higher-priority task is blocked by a lower-priority task, causing delays.
- Buffer Overflow
Occurs when more data is written to a buffer than it can hold, potentially crashing a system.
- Noise Handling
Techniques utilized to address data corruption caused by external interference.
Reference links
Supplementary resources to enhance your learning experience.
