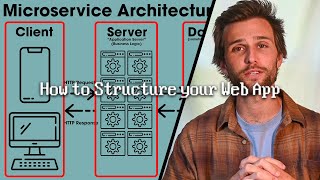
Protocol Design and Custom Application Layer
Enroll to start learning
You’ve not yet enrolled in this course. Please enroll for free to listen to audio lessons, classroom podcasts and take practice test.
Interactive Audio Lesson
Listen to a student-teacher conversation explaining the topic in a relatable way.
Basics of Protocol Design
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Today we will discuss protocol design. Can anyone tell me what a protocol is?

Is it like a set of rules for communication between computers?

Exactly, Student_1! Protocols are essential as they define the rules and conventions for communication. Can anyone give an example of a well-known protocol?

HTTP? It's used for web communication!

Great job! HTTP is a perfect example. Now, what do you think makes a communication protocol effective?

I think it should be clear and easy to understand.

Exactly! Clarity and structure are vital. Remember: 'Clear Communication is Key' can help you remember this principle.

What about using binary formats versus text formats?

Excellent question! We will cover the pros and cons of both in our next session.
Text and Binary Formats
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Now, let's move on to data formats in protocols. Why do you think someone might choose a binary format over a text format?

Binary formats can be more efficient in terms of size?

Exactly! Binary formats are compact and faster to transmit. Can anyone think of a situation where text formats might be better?

Text formats are easier to read and debug.

Correct! For example, when developing or troubleshooting, human-readable formats are very beneficial.

So, it depends on the use case?

Yes! Always consider the use case. Let's recap: 'Binary for Speed, Text for Clarity'.
Example Protocol Design
🔒 Unlock Audio Lesson
Sign up and enroll to listen to this audio lesson

Now that we know about formats, let’s look at a simple protocol example. Imagine a client sends a LOGIN request with credentials.

What would that look like?

Great question! It would be something like: 'LOGIN username password'. What do you think the server would reply with?

'200 OK' if it’s successful, and maybe '401 Unauthorized' if not?

Exactly! You’ve grasped the key elements. Remember: 'Success is 200, Failure is 401'. How could such a protocol be useful?

It helps ensure both the client and server understand each other!

Exactly right, Student_2! This interaction solidifies the importance of a well-defined protocol in application communication.
Introduction & Overview
Read summaries of the section's main ideas at different levels of detail.
Quick Overview
Standard
Understanding how to design custom application protocols is crucial for network programming. This section illustrates the concept by providing examples of simple command exchanges between a client and server, emphasizing the significance of a well-structured protocol in delivering operational functionality.
Detailed
Detailed Summary
In the realm of network programming, designing your own application-level protocols is a valuable skill. At its core, a protocol is a set of rules that enables communication over a network. In this section, we explore how custom protocols can be defined using either text or binary formats.
The discussion begins with a simplistic example where a client communicates with a server by sending a LOGIN command followed by a username and password. The server, upon receiving this information, responds with status codes (e.g., 200 OK for successful login or 401 Unauthorized if the credentials are incorrect).
This paradigm exemplifies the importance of clear communication rules and structures within networked applications, ensuring that both the client and server understand the protocol and can react accordingly. Furthermore, it underscores the significance of protocols in establishing a reliable relationship between components in a network.
This foundational knowledge in protocol design is crucial for developing more complex applications, enabling developers to create robust, efficient communication systems that are adaptable to various data transmission formats.
Youtube Videos






Audio Book
Dive deep into the subject with an immersive audiobook experience.
Defining Custom Protocols
Chapter 1 of 2
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
You can define your own application-level protocols using text or binary formats.
Detailed Explanation
In network programming, defining your own application-level protocols means creating rules or formats that dictate how data should be structured and communicated between servers and clients. This can use either readable text formats (like JSON or XML) or binary formats (which are more compact and faster to process). For instance, you might specify that a client sends login requests in a certain way, allowing the server to understand and respond appropriately.
Examples & Analogies
Think of defining a custom protocol like establishing a secret handshake with a friend. Just as you and your friend have agreed upon specific movements to confirm each other's identity, a custom protocol sets the rules for communication between the server and client, making sure they both 'understand' each other.
Example of a Simple Protocol
Chapter 2 of 2
🔒 Unlock Audio Chapter
Sign up and enroll to access the full audio experience
Chapter Content
Example: Client → Server: LOGIN username password Server → Client: 200 OK or 401 Unauthorized
Detailed Explanation
This example illustrates a simple protocol used for logging into a system. The client sends a message structured as 'LOGIN username password' to the server. The server then processes this request and responds with '200 OK' if the credentials are valid, or '401 Unauthorized' if they are not. This two-way communication is an integral part of how many applications authenticate users, ensuring that only valid users can access protected resources.
Examples & Analogies
Imagine trying to enter a club. You approach the bouncer (the server) and say, 'I’d like to enter, my name is John Doe.' If your name is on the guest list (valid username and password), the bouncer lets you in (200 OK). If you’re not on the list, the bouncer tells you you can’t enter (401 Unauthorized). This interaction mirrors the login example, where specific requests and responses determine access.
Key Concepts
-
Protocol Design: The process of defining a set of rules for communication.
-
Application-Level Protocols: Protocols that operate at the application layer.
-
Custom Protocol: A tailor-made protocol to suit specific communication needs.
Examples & Applications
Client sends: 'LOGIN user pass'; Server responds: '200 OK' or '401 Unauthorized'.
Defining your own message formats can streamline data exchange in applications.
Memory Aids
Interactive tools to help you remember key concepts
Rhymes
When you set the rules, keep it neat, or no one can connect, and that’s a feat!
Stories
Imagine a post office where every letter has specific instructions to ensure it reaches the right address—that's how protocols help data reach its destination!
Memory Tools
Remember the phrase 'Success is 200, Failure is 401' to recall protocol responses.
Acronyms
C3
Clarity
Consistency
Compactness—that’s what a good protocol needs!
Flash Cards
Glossary
- Protocol
A set of rules that defines how data is transmitted over a network.
- Application Layer
The top layer in the OSI model, where application-level protocols operate.
- LOGIN Command
A request structure sent by a client to authenticate a user.
- Status Code
A code sent by the server to indicate the result of a client's request.
Reference links
Supplementary resources to enhance your learning experience.
